Mapping Standards Components to API Security Framework
API Concepts section of this standard define the following components
- API Provider
- API Consumer
- Health Sector Participants (human)
- Health Sector Organisation
- Health Workers
- API Designers
- API Developers
The two standards that Health NZ SHOULD use to protect and secure API resources are OAuth 2.0 and OpenID Connect.
OpenID Connect adds Identity to the mix and is built on OAuth 2.0 but uses a different naming standard to define similar capabilities.
This section captures the key components of these standards to help clarify the similarities and differences between the two standards.
On top of these, additional standards have been defined that focus on additional security features and enhancements.
OAuth 2.0
Overview
The fundamental components of a solution using the OAuth 2.0 framework are illustrated below.
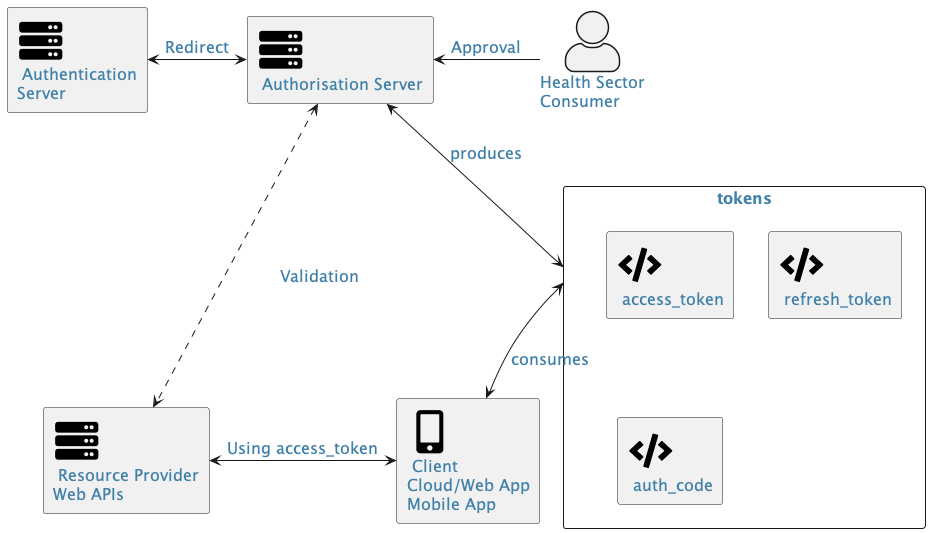
Detailed description of figure
The diagram depicts a typical OpenID Connect authentication and authorization flow, where a user grants approval to an oidc provider, which then redirects to an authentication server. After successful authentication, tokens are issued and used by a client application to access protected resources.
Applicability
The OAuth 2.0 standard defines a foundation for delegated authority which designers/implementers of health sector API solutions SHOULD build on. It is important to note that OAuth 2.0 leverages external authentication and authorisation services to enable mobile / web applications to act with the delegated authority of a user. OAuth 2.0 uses security tokens (and information related to the token) to authorise access to a protected resource, without requiring the owner of the data (e.g. a patient and their records) to have to share their sensitive credentials.
OAuth 2.0 provides a more comprehensive and extensible approach to security than some of the basic authentication and authorisation mechanisms.
Although OAuth 2.0 is used in consent and delegation flows it expects the following two areas to be covered outside the OAuth 2.0 standard:
- Authentication of the End User / Resource Owner when they login (using their credentials) to provide consent, normally delivered via a redirect
- Capturing and Management of the consent request and approval process or the consent itself which defines specific permissions (e.g. read) to the client (application) that wants access a resource API
Other API Security Standards are layers on top of OAuth 2.0 to provide additional functionality or features to address security concerns. This can increase the complexity and performance of the solution therefore it is important to select the required API security architecture to:
- Match the type of resource, for example a Patient record or a list of GPs in Wellington
- The risk involved (Exposure of personal data)
- The application architecture from which the API is being called, e.g. Mobile, Native or Web application
OAuth 2.0 versions
Designers and implements of APIs SHOULD follow the recommendations in the table below when considering the OAuth 2.0 version to use.
| OAuth 2.0 version | Summary | When to use |
|---|---|---|
| 1.0a | OAuth 1.0a is derived from the original OAuth 1.0 specification (RFC 5849) which provided a method for client applications to access resources on behalf of a resource owner. It forms an authentication framework for exchange of signed tokens. | This version was made obsolete by OAuth 2.0. and SHOULD NOT be used by NZ health sector APIs💡 |
| 2.0 | OAuth 2.0 is an open standard framework for delegated authorisation, based on token exchange. It is not backward-compatible with OAuth 1.0, the primary difference being that it secures tokens by mandating TLS on all communication connections (RFC 6749) (instead of OAuth 1.0 digital signatures) | This is the current standard but is being superseded by version 2.1. NZ health sector APIs SHOULD use this standard as the base framework for their API security architecture💡 |
| 2.1 | This update to OAuth 2.0 tightens the supported flows and applies additional security. | This is expected to become the standard and NZ health sector APIs SHOULD therefore review and support this specification. If misalignment with OAuth 2.0 or ambiguity arises, API designers/developers are advised to implement the OAuth 2.1 recommendations.💡 |
OpenID Connect (OIDC)
OpenID Connect is the recommended security profile for the use of OAuth 2.0 authentication security tokens when an API requires more secure authentication e.g. when data is a two-way flow between the consuming application and the API. (e.g. read and write). It introduces the concept of Identity in the form of an ID token that can contain information about the end user which can be used to:
-
Enhance the process and user experience during the onboarding process
-
Provide an SSO capability
-
Secure transfer of user data
-
Enrich the user experience
-
Provides a trust framework [integrity] for Service and Identity Providers to share consented user data
OpenID Connect's fundamental security components are similar to OAuth 2.0, just having different names. The only significant difference from OAuth 2.0 is the ID token as highlighted in the diagram below.
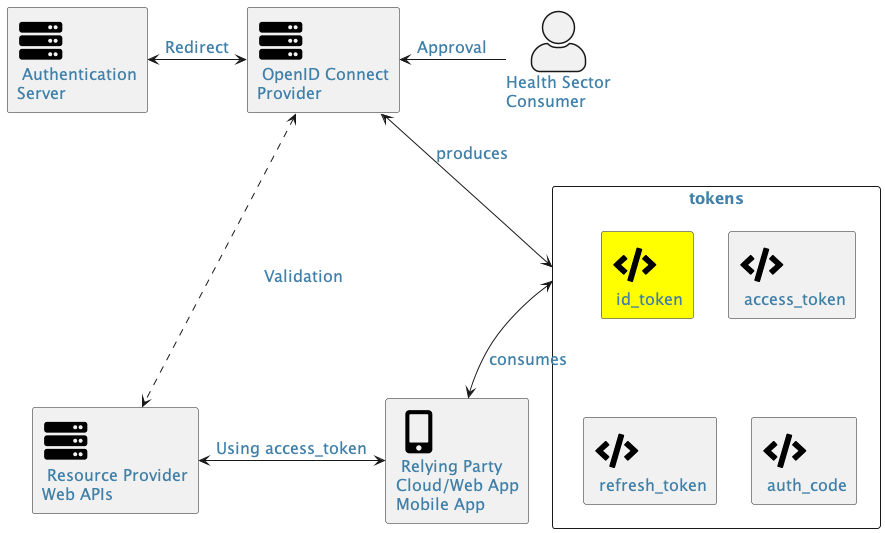
Detailed description of figure
The diagram depicts a typical OpenID Connect authentication and authorization flow, where a user grants approval to an oidc provider, which then redirects to an authentication server. After successful authentication, tokens are issued and used by a client application to access protected resources. The diagram is similar to the previous diagram with the addition of an id token
| Oauth 2.0 Component | OpenID Connect Component | API Standards Component | Description |
|---|---|---|---|
| Resource Owner | End UserCustomer | Health Sector Participant | |
| Client (Application) | Relying Party | API Consumer | |
| OAuth 2.0 Server Authorisation Server | OpenID Provider ServerAuthorisation Server | Owned by a Health Sector Organisation | |
| Authentication Server | Authentication Server | Owned by a Health Sector Organisation | |
| Resource Server/ Provider | Resource Server/ Provider | API Provider | A resource server hosts protected resources (APIs & backend applications) which only allow authenticated and authorised clients by: |